Why should i use Proxy server?
Open Wi-Fi Connections:
It is possible for anyone to monitor everything you do on an Open Wi-Fi Network. Not all sites that you visit may use HTTPS Encryption. Sometimes even sites that do use HTTPS only do so for certain actions and then revert to regular unencrypted HTTP connections, which are visible by anyone on the network. Using a proxy server will direct all web traffic through a secure and encrypted tunnel making all of your browsing safe and unseeable.
Bypass Firewalls and Corporate Web Filtering:
Users who wish to bypass web monitoring and restrictions imposed by their employer may utilize Proxy Servers. This is great for users and dangerous for IT Professionals as it may pose a danger to network security.
How to Set up the proxy server using Hamachi and Privoxy?
Requirements:
- 2 computers. One works proxy server. Other one use the proxy server(client). Both system should have Internet connection.
- Hamachi: A free (for non-commercial use), cross-platform VPN service that, gives you secure access to your home network no matter where you are. Download it from here:
https://secure.logmein.com/products/hamachi2/
- Privoxy: A free, Privoxy is a non-caching web proxy with advanced filtering capabilities for enhancing privacy, modifying web page data and HTTP headers, controlling access, and removing ads and other obnoxious Internet junk. Privoxy has a flexible configuration and can be customized to suit individual needs and tastes. It has application for both stand-alone systems and multi-user networks. Download it from here:
http://www.privoxy.org/
Installing Hamachi and Set up the Server
Step 1:
Decide which Computer is going to work as Proxy Server. Install the Hamachi in that computer.
Step 2:
Once you installed, run the application. It will open small Hamachi application window with thanks message.
Step 3:
Click the Power Button. It will automatically detect the host name and ask you to register the client.
Once you registered, it will show some IP address like 5.xx.xxx.xxx near to the power button. Note this is our proxy ip Address.
Step 4:
Now you will get two options. 1. Create New Network 2.Join an existing Network.
This is server Computer, we have to create network to used by client.
So click the
Create a New Network button.
Step 5:
It will ask you to enter network id and password(i entered id as proxy_BreakTheSecurity). Enter your desire id and password(Should be strong password).
Click the Create button.
That's all your server is ready to be used.
Using Our Proxy Server in client Side
Now move to your client system( i mean any other computer). Install Hamachi in your that system.
Follow the first three step mentioned above.
Step 4:
Now you will get two options. 1. Create New Network 2.Join an existing Network.
This is Client System, right? so Click the Join an Existing network.
Step 5:
Enter the Network id and password that you used to create network. (in my case, network id i entered is proxy_BreakTheSecurity)
You can rinse and repeat this on every machine you want to do this with, for up to 16 clients (that’s the limit for Hamachi’s free-for-non-commercial-use version)
Installing the Privoxy in the client system:
Install the privoxy and run.
Step 1:
In system tray, you can see
P icon. right click on the P
and select
Edit->Main Configuration.
Step 2:
It will open the config.txt file in notepad.
Search for the "listen-address 127.0.0.1:8118"
Replace the 127.0.0.1 with our proxy ip address(address that displayed in server hamachi apps) created in server side.
For example listent-address
5.xx.xxx.xxx:8118
Save the file.
That's all you finished. Restart the privoxy.
Now we have to use the Proxy server.
Set Up Your Web Browser to Use Your New Secure Proxy:
Open the Mozilla Firefox
Open Tools->Preferences.
It will open the preference window of Firefox.
Select Advanced->Network tab.
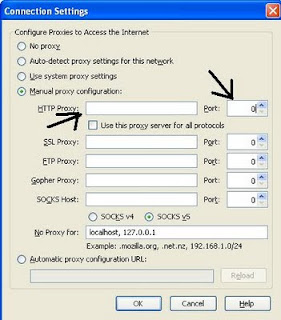
Click the Settings button near to the "Configure how Firefox connects to the Internet”
Select the Manual proxy configuration.
Enter our Server Proxy Address(5.xx.xxx.xx) and port as 8118.
click ok.
Test the Proxy Server.
Now we have to test whether our proxy is working or not.
Visit http://config.privoxy.org/. It will detect whether you use proxy or not.
If proxy is used, you’ll see a message like “This is Privoxy 3.0.17 on Windows (5.xxx.xxx.xx), port 8118, enabled.”
If not, you’ll see a page that reads “Privoxy is not being used”.
Also, if you’re on a public Wi-Fi connection and you navigate to something like WhatIsMyIP.com with your proxy turned off, you should see a different IP when you reload the page with your proxy turned on.
(Essentially, when turned on, your home’s public IP address should be showing.)
Even though your proxy is running over an HTTP connection, Hamachi is encrypting everything that runs between your computers, so it’s still a secure option
![[Image: 86437852.png]](http://img69.imageshack.us/img69/342/86437852.png)
![[Image: 79399926.png]](http://img846.imageshack.us/img846/2103/79399926.png)
![[Image: 12150512.png]](http://img38.imageshack.us/img38/1104/12150512.png)
![[Image: 21993618.png]](http://img412.imageshack.us/img412/8135/21993618.png)
![[Image: 48030887.png]](http://img24.imageshack.us/img24/3928/48030887.png)
![[Image: 42338878.png]](http://img849.imageshack.us/img849/3088/42338878.png)
![[Image: 20865461.png]](http://img207.imageshack.us/img207/6392/20865461.png)
![[Image: 72909853.png]](http://img64.imageshack.us/img64/5939/72909853.png)
![[Image: 39811637.png]](http://img24.imageshack.us/img24/5476/39811637.png)
![[Image: 66665680.png]](http://img267.imageshack.us/img267/2707/66665680.png)
![[Image: 38943479.png]](http://img337.imageshack.us/img337/2769/38943479.png)
![[Image: 77928950.png]](http://img840.imageshack.us/img840/2060/77928950.png)